You can now spam JPEGs in Bitcoin private keys
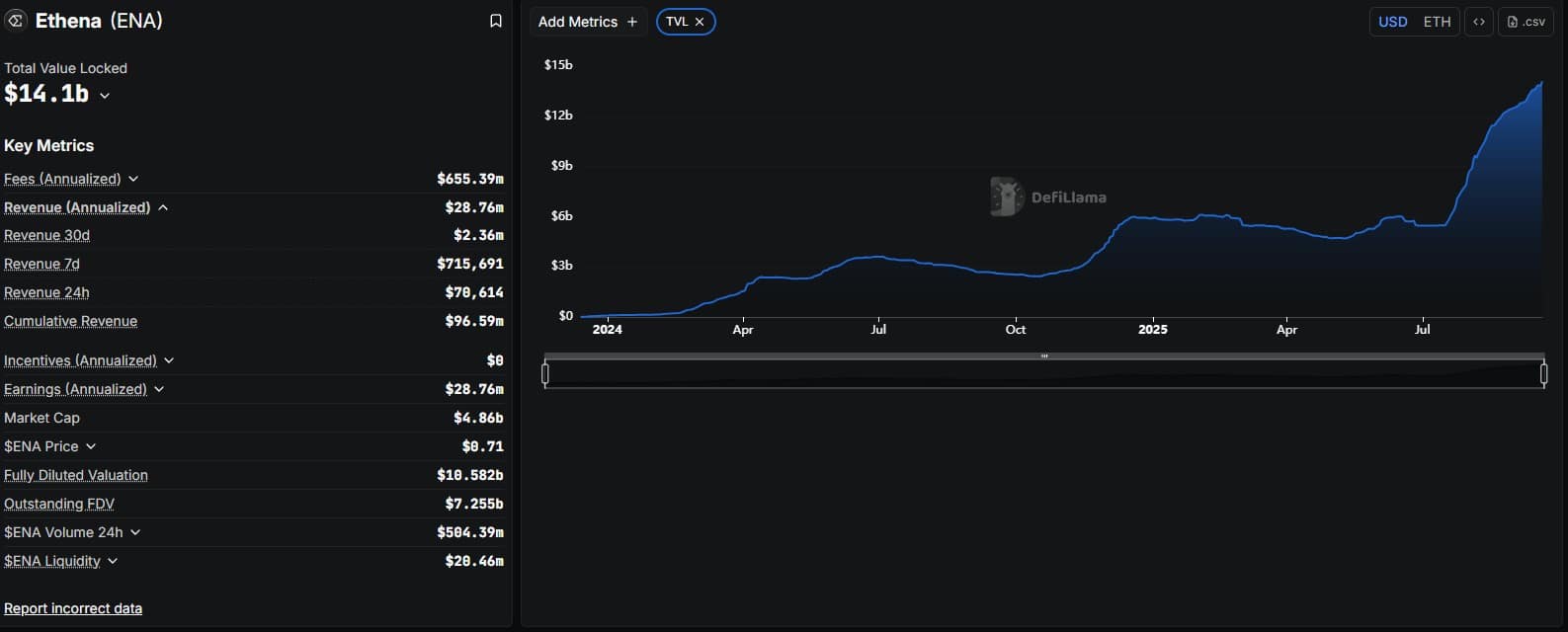
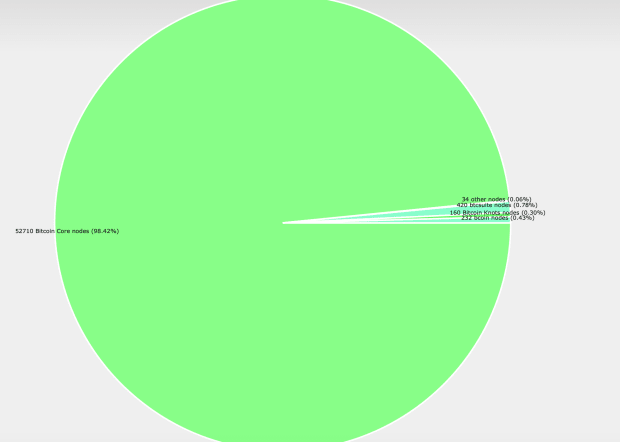
The post You can now spam JPEGs in Bitcoin private keys appeared on BitcoinEthereumNews.com. Developers in favor of the contentious Bitcoin Core version 30 software update cheered today when a cryptographer invented a new way to spam Bitcoin’s blockchain with images without using OP_RETURN. After months of civil war over the proper limitations of this scripting tool, this new method showed that even reducing OP_RETURN’s datacarrier allowance to zero would not prevent all forms of arbitrary data storage. OP_RETURN is the most popular storage area for large quantities of data unrelated to the on-chain movement of BTC. Core is fighting with a forked client of its node software, Knots, about the maximum amount of arbitrary data that the two camps will relay around the Bitcoin network’s queues of pending transactions or ‘mempools.’ Core version 30 will update the default datacarrier threshold to nearly 1MB, whereas Knots prefers a number closer to 80 bytes. Unfortunately, as today’s discovery proves, neither setting can guarantee against all forms of on-chain spam. Specifically, the cryptographer stored a JPEG image mostly inside of a cleverly modified private key. Spamming Bitcoin’s blockchain with images inside private keys Indeed, BitMEX Research created a transaction containing a JPEG mostly stored within a private key—not an OP_RETURN output. Researchers deliberately used an insecure private key that could be derived solely from on-chain data on the Bitcoin blockchain itself, so that in a sense the image was stored on the blockchain. The clever method proves that motivated users looking to store arbitrary data on the ledger can bypass OP_RETURN entirely and store data using keypairs that are consensus valid and impossible to filter out. Read more: Bitcoin Core devs think it would be easy, and funny, to attack Knots Although the method is unique and clever in the history of cryptography, some people hearked all the way back to Claude Shannon’s 1940s work on…

The post You can now spam JPEGs in Bitcoin private keys appeared on BitcoinEthereumNews.com.
Developers in favor of the contentious Bitcoin Core version 30 software update cheered today when a cryptographer invented a new way to spam Bitcoin’s blockchain with images without using OP_RETURN. After months of civil war over the proper limitations of this scripting tool, this new method showed that even reducing OP_RETURN’s datacarrier allowance to zero would not prevent all forms of arbitrary data storage. OP_RETURN is the most popular storage area for large quantities of data unrelated to the on-chain movement of BTC. Core is fighting with a forked client of its node software, Knots, about the maximum amount of arbitrary data that the two camps will relay around the Bitcoin network’s queues of pending transactions or ‘mempools.’ Core version 30 will update the default datacarrier threshold to nearly 1MB, whereas Knots prefers a number closer to 80 bytes. Unfortunately, as today’s discovery proves, neither setting can guarantee against all forms of on-chain spam. Specifically, the cryptographer stored a JPEG image mostly inside of a cleverly modified private key. Spamming Bitcoin’s blockchain with images inside private keys Indeed, BitMEX Research created a transaction containing a JPEG mostly stored within a private key—not an OP_RETURN output. Researchers deliberately used an insecure private key that could be derived solely from on-chain data on the Bitcoin blockchain itself, so that in a sense the image was stored on the blockchain. The clever method proves that motivated users looking to store arbitrary data on the ledger can bypass OP_RETURN entirely and store data using keypairs that are consensus valid and impossible to filter out. Read more: Bitcoin Core devs think it would be easy, and funny, to attack Knots Although the method is unique and clever in the history of cryptography, some people hearked all the way back to Claude Shannon’s 1940s work on…
What's Your Reaction?